kubectl create cm cm11 --from-literal=key1=value1 -o yaml
create one yml file
apiVersion: v1
data:
key1: value1
key2: value2
key3: value3
key4: value4
kind: ConfigMap
metadata:
name: cm9999
~ kubectl apply -f cm6.yml


Tutorials on DevOps Technologies including Bugzilla, Chef, Docker, Git, Jira, Kubernetes, Puppet, SaltStack, Scrapy, Unix
kubectl create cm cm11 --from-literal=key1=value1 -o yaml
create one yml file
apiVersion: v1
data:
key1: value1
key2: value2
key3: value3
key4: value4
kind: ConfigMap
metadata:
name: cm9999
~ kubectl apply -f cm6.yml
vi env.sh
variable1=value1
variable2=value2
variable3=value3
variable4=value4
kubectl create cm cm7 --from-env-file=env.sh
kubectl get cm
NAME DATA AGE
cm1 0 36m
cm2 0 36m
cm3 1 30m
cm4 2 23m
cm5 3 11m
cm6 1 2m4s
cm7 4 3s
kubectl create cm cm6 --from-file=env.sh
variables name cannot be started from numbers
e.g
355 variables=value1 >> wrong method
create 3 files
echo "file1" > test1.properties
echo "file2" > test2.properties
echo "file3" > test3.properties
kubectl create cm cm5 --from-file=properties/
$ kubectl describe cm cm5
Name: cm5
Namespace: default
Labels: <none>
Annotations: <none>
Data
====
test1.properties:
----
file1
test2.properties:
----
file2
test3.properties:
----
file3
Events: <none>
vi application.properties
**********************************
# database details
database_ip="192.168.0.4"
database_password="moon"
database_username="abid"
# admin details
username=moonadmin
pasword=moonpassword
************************************
kubectl create cm cm3 --from-file=application.properties
output:
NAME DATA AGE
cm1 0 6m12s
cm2 0 6m6s
cm3 1 12s
controlplane $ kubectl describe cm3
error: the server doesn't have a resource type "cm3"
controlplane $ kubectl describe cm cm3
Name: cm3
Namespace: default
Labels: <none>
Annotations: <none>
Data
====
application.properties:
----
# database details
database_ip="192.168.0.4"
database_password="moon"
database_username="abid"
# admin details
username=moonadmin
pasword=moonpassword
secound example :
vi moon.properties
# database details
database_ip="192.168.0.4"
database_password="moon"
database_username="abid"
added two config files
kubectl create cm cm4 --from-file=moonabid.properties --from-file=application.properties
ConfigMaps are APIs that store configuration data in key-value pairs. Their primary function is to keep the configuration separate from the container image. It can represent the entire configuration file or individual properties.
If you are working with Kubernetes, you want to keep your image light and portable. To do this, you should keep the configuration settings separate from the application code. Using ConfigMaps you can add different configuration data on pods to suit the environment they are running in.
For example, you may use the same code with different configuration while in the development, testing or production phase.
You can create ConfigMaps from files, directories, and literal values.
The basic syntax for creating a ConfigMap is:
kubectl create configmap [configmap_name] [attribute] [source]Depending on the source, the attribute will be:
--from file (if the source is a file/directory)--from-literal (if the source is a key-value pair)Use a .yaml file that contains the wanted configuration in the format of key-value pairs to create a ConfigMap:
kubectl create configmap [configmap_name] --from-file [path/to/yaml/file]For example, to create a ConfigMap under the name example-configmap from the example-configmap.yaml file, you would run:
kubectl create example-configmap --from-file /api/v1/namespace/default/configmaps/example-configmap.yamlKubernetes allows creating a ConfigMap from one or multiple files in any plaintext format (as long as the files contain key-value pairs).
To create a ConfigMap from a file, use the command:
kubectl create configmap [configmap_name] --from-file [path/to/file]To create a ConfigMap from multiple files, run:
kubectl create configmap [configmap_name] --from-file [path/to/file1] --from-file [path/to/file2] --from-file [path/to/file3]You can also create ConfigMaps from directories, that is from all the files within the directory. To do so, use the command:
kubectl create configmap [configmap_name] --from-file [path/to/directory]Kubectl packages each file from the directory into the new ConfigMap. Only files with basenames that are valid keys are included. Subdirectories and non-regular files are not included in the ConfigMap.
You can also create ConfigMaps from literal values, using the --from-literal option.
To do so, follow the basic syntax:
kubectl create configmap [configmap_name] --from-literal [key1]=[value1] --from-literal [key2]=[value]2To see details from a Kubernetes ConfigMap and the values for keys, use the command:
kubectl get configmaps [configmap_name] -o yamlThe output should display information in the yaml format:
apiVersion: v1
data:
key1: value1
key2: value2
...
kind: ConfigMap
metadata:
creationTimeStamp: ...
name: example-configmap
namespace: default
resourceVersion: ...
selfLink: /api/v1/namespace/default/configmaps/example-configmap
uid: ...There are two ways you can configure a pod to use a specific ConfigMap:
Once you have downloaded or created a ConfigMap, you can mount the configuration to the pod by using volumes.
Add a volume section to the to the yaml file of your pod:
volumes:
- name: config
configMap
name: [configmap_name]
items:
- key: [key/file_name]
path: [inside_the_pod]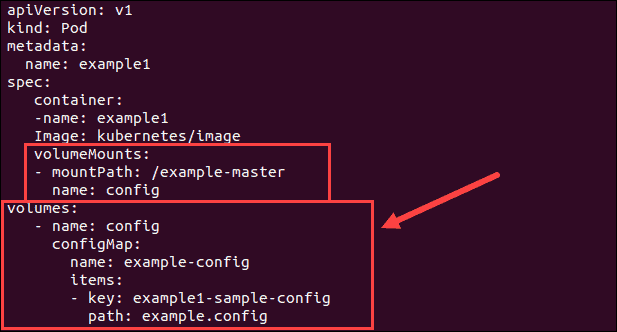
Once you have added the required content, use the kubectl create command to create the pod with the ConfigMap as the volume.
ConfigMaps allows you to introduce multiple values through environment variables.
Add the env section to the yaml file of the pod to pull the specified environment variable(s) from a ConfigMap:
env:
- name: SPECIAL_LEVEL_KEY
valueFrom:
configMapKeyRef:
name: [configmap_name]
key: [key/file_name]To pull all environment variables from a ConfigMap, add the envFrom section to the yaml file:
envFrom:
- configMapKeyRef
name: env-config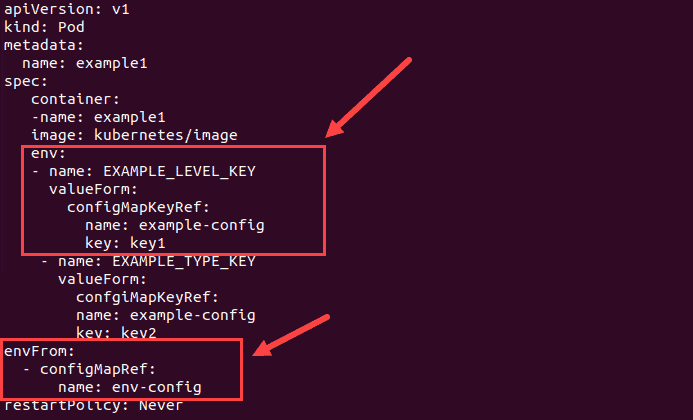
Then, use the kubectl create command to create the pod with the specified configuration settings.
Conclusion
This article showed you four different ways how to create ConfigMaps. Additionally, it includes two ways of using Kubernetes ConfigMaps with pods.
kubectl get cm
kubectl create cm cm1 --from-literal=database_ip="192.168.0.4"
key = value
Name: cm1
Namespace: default
Labels: <none>
Annotations: <none>
Data
====
database_ip:
----
192.168.0.4
Events: <none>
vi moon.yml
****************************
apiVersion: v1
kind: ResourceQuota
metadata:
name: pods-medium
spec:
hard:
requests.cpu: 0.5
requests.memory: 500Mi
limits.cpu: 1
limits.memory: 1Gi
*************************************
kubectl apply -f moon.yml -n tester
********************************************
create one more pod
vi abid.yml
apiVersion: v1
kind: Pod
metadata:
name: moon
spec:
containers:
- name: web-server
image: nginx
resources:
requests:
memory: 250Mi
cpu: 0.1
limits:
cpu: 0.5
memory: 500Mi
kubectl apply -f abid.yml -n tester
kubectl describe ns tester
A resource quota, defined by a ResourceQuota the object provides constraints that limit aggregate resource consumption per namespace. It can limit the number of objects that can be created in a namespace by type, as well as the total amount of computing resources that may be consumed by resources in that namespace.
create one namespace.
kubectl create namespace developer
apiVersion: v1
kind: ResourceQuota
metadata:
name: pods-medium
spec:
hard:
pods: "10"
kubectl apply -f quota.yml -n developer
kubectl describe ns developerName: developer
Labels: <none>
Annotations: <none>
Status: Active
Resource Quotas
Name: pods-medium
Resource Used Hard
-------- --- ---
pods 0 10
create namespace
kubectl create namespace test-team
vi moon.yml
*******************************************
apiVersion: v1
kind: Pod
metadata:
name: pod1
namespace: test-team
labels:
tier: frontend
spec:
containers:
- name: podngin
image: nginx
0r
kubectl delete pod pod1 -n test-team
how to change default NameSpace ?
kubectl config set-context --current --namespace=test-team
apiVersion: v1
kind: Pod
metadata:
name: quota
labels:
app: myapp
type: frontend
spec:
containers:
- name: pod-quota
image: nginx
resources:
requests:
memory: 200Mi
cpu: 100m
vi moon.yml
________________________________
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 4
minReadySeconds: 30
strategy:
rollingUpdate:
maxSurge: 3
maxUnavailable: 0
type: RollingUpdate
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.14.2
ports:
- containerPort: 80
kubectl apply -f moon.yml
__________________________((((((((((((((((((((((((((((())))))))))))))))))____________________
change version of nginx
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 4
minReadySeconds: 30
strategy:
rollingUpdate:
maxSurge: 3
maxUnavailable: 0
type: RollingUpdate
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.14.3
ports:
- containerPort: 80
kubectl apply -f moon.yml --record=true
kubectl explain deployment nginx-deployment
kubectl rollout history deploy nginx-deployment
output :
deployment.apps/nginx-deployment
REVISION CHANGE-CAUSE
2 kubectl apply --filename=dep.yml --record=true
3 kubectl apply --filename=dep.yml --record=true
kubectl rollout history <name of deployment> --revision =2
kubectl rollout undo <name of deployment> --revision =2
vi moon.yml
______________________________________________________
apiVersion: apps/v1
kind: ReplicaSet
metadata:
name: abid-moon
labels:
app: guestbook
tier: frontend
spec:
# modify replicas according to your case
replicas: 3
selector:
matchLabels:
tier: frontend
template:
metadata:
labels:
tier: frontend
spec:
containers:
- name: moon-solutions
image: nginx
++++++++++++++++++++++++++++++++++++++++++++++++++
apiVersion: v1
kind: Pod
metadata:
name: pod2
labels:
app: guestbook
spec:
containers:
- name: podngin
image: nginx
~
++++++++++++++++++++++++++++++++
+++++++++++++++++++++++++++++++
apiVersion: v1
kind: Pod
metadata:
name: pod2
labels:
tier: frontend
spec:
containers:
- name: podngin
image: nginx
+++++++++++++++++++++++++++++++++++
~
vi moon.yml
***************************************************
apiVersion: v1
kind: ReplicationController
metadata:
name: nginx
spec:
replicas: 7
selector:
type: nginx
template:
metadata:
name: nginx
labels:
type: nginx
spec:
containers:
- name: nginx
image: nginx
| Step1: On All Machines ( Master & All nodes ): | |
| ********************** | |
| ### INSTALL DOCKER | |
| sudo apt-get update | |
| sudo apt-get install -y apt-transport-https ca-certificates curl software-properties-common | |
| curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add - | |
| sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable" | |
| sudo apt-get update ; clear | |
| sudo apt-get install -y docker-ce | |
| sudo service docker start ; clear | |
| ### INSTALL KUBEADM,KUBELET,KUBECTL | |
| echo "deb http://apt.kubernetes.io/ kubernetes-xenial main" | sudo tee /etc/apt/sources.list.d/kubernetes.list | |
| curl -s https://packages.cloud.google.com/apt/doc/apt-key.gpg | sudo apt-key add - | |
| sudo apt-get update ; clear | |
| sudo apt-get install -y kubelet kubeadm kubectl | |
| ************************ | |
| Step2: On Master only: | |
| *********************** | |
| sudo kubeadm init --ignore-preflight-errors=all | |
| sudo mkdir -p $HOME/.kube | |
| sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config | |
| sudo chown $(id -u):$(id -g) $HOME/.kube/config | |
| ## Weave | |
| ********************** | |
| kubectl apply -f "https://cloud.weave.works/k8s/net?k8s-version=$(kubectl version | base64 | tr -d '\n')" | |
| kubectl get nodes | |
| kubectl get all --all-namespaces | |
| ********************** | |
| Step3: On Nodes only: | |
| ********************** | |
| copy the kubeadm join token from master & run it on all nodes | |
| Ex: kubeadm join 10.128.15.231:6443 --token mks3y2.v03tyyru0gy12mbt \ | |
| --discovery-token-ca-cert-hash sha256:3de23d42c7002be0893339fbe558ee75e14399e11f22e3f0b34351077b7c4b56 | |
| how to find kubeadm join token later | |
| **************************** | |
| kubeadm token create --print-join-command --ttl=0 | |
## Install Kubernetes on CENTOS | |
| ### Step1: `On All Machines ( Master & All nodes ):` | |
| ### Set SELinux in permissive mode (effectively disabling it) | |
| setenforce 0 | |
| sed -i 's/^SELINUX=enforcing$/SELINUX=permissive/' /etc/selinux/config | |
| ### Install Docker | |
| sudo yum remove -y docker docker-client docker-client-latest docker-common docker-latest docker-latest-logrotate docker-logrotate docker-engine docker-ce docker-ce-cli containerd.io | |
| sudo yum install -y yum-utils device-mapper-persistent-data lvm2 | |
| sudo yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo | |
| sudo yum install -y docker-ce docker-ce-cli containerd.io | |
| systemctl enable --now docker | |
| systemctl start docker | |
| ### Install kubeadm,kubelet,kubectl | |
| cat <<EOF > /etc/yum.repos.d/kubernetes.repo | |
| [kubernetes] | |
| name=Kubernetes | |
| baseurl=https://packages.cloud.google.com/yum/repos/kubernetes-el7-x86_64 | |
| enabled=1 | |
| gpgcheck=1 | |
| repo_gpgcheck=1 | |
| gpgkey=https://packages.cloud.google.com/yum/doc/yum-key.gpg https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg | |
| EOF | |
| yum install -y kubelet kubeadm kubectl --disableexcludes=kubernetes | |
| systemctl enable --now kubelet | |
| ### Step2: `On Master only:` | |
| sudo kubeadm init --ignore-preflight-errors=all | |
| sudo mkdir -p $HOME/.kube | |
| sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config | |
| sudo chown $(id -u):$(id -g) $HOME/.kube/config | |
| ## Weave Pod Network | |
| kubectl apply -f "https://cloud.weave.works/k8s/net?k8s-version=$(kubectl version | base64 | tr -d '\n')" | |
| kubectl get nodes | |
| kubectl get all --all-namespaces | |
| ### Step3: `On Nodes only:` | |
| copy the kubeadm join token from master & run it on all nodes | |
| Ex: kubeadm join 10.128.15.231:6443 --token mks3y2.v03tyyru0gy12mbt \ | |
| --discovery-token-ca-cert-hash sha256:3de23d42c7002be0893339fbe558ee75e14399e11f22e3f0b34351077b7c4b56 | |
| ##### To Generate certificate or public key | |
| openssl x509 -pubkey -in /etc/kubernetes/pki/ca.crt | openssl rsa -pubin -outform der 2>/dev/null | openssl dgst -sha256 -hex | sed 's/^.* //' | |